Deep Learning Security for IoT
Han Wu, University of Exeter, the U.K.
Research Website
Background
Is Deep Learning secure for IoT?
Deep Learning on IoT Edge Devices

 Autonomous Driving: The IoT in Automotive
Autonomous Driving: The IoT in Automotive
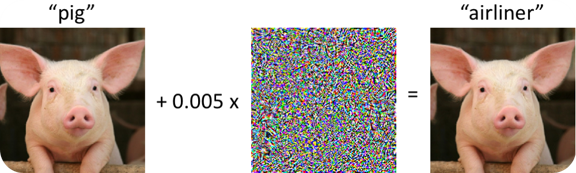
Adversarial attacks against image classification [1]
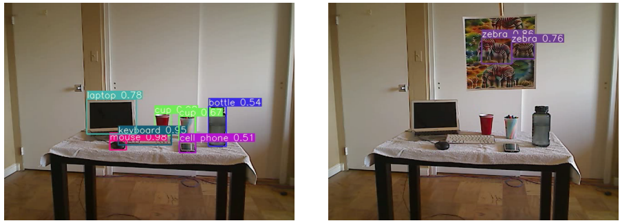 Adversarial attacks against object detection
Adversarial attacks against object detection
[1] J. Z. Kolter and A. Madry, Adversarial Robustness - Theory and Practice, NeurIPS 2018 tutorial.
Deep Learning Models are vulnerable to Adversarial Attacks.
1. High-End: Linux
2. High-End: RT-Thread Smart
3. Middle-End: RT-Thread
IoT Devices consist of High-End, Middle-End, and Low-End Devices.
Adversarial Detection
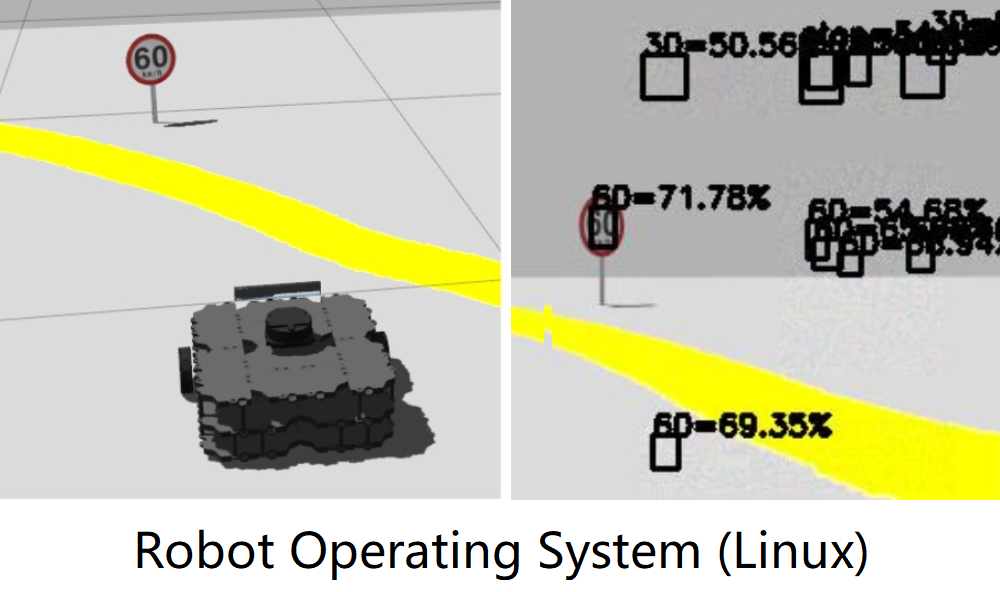
Attacking Object Detection in Real Time.
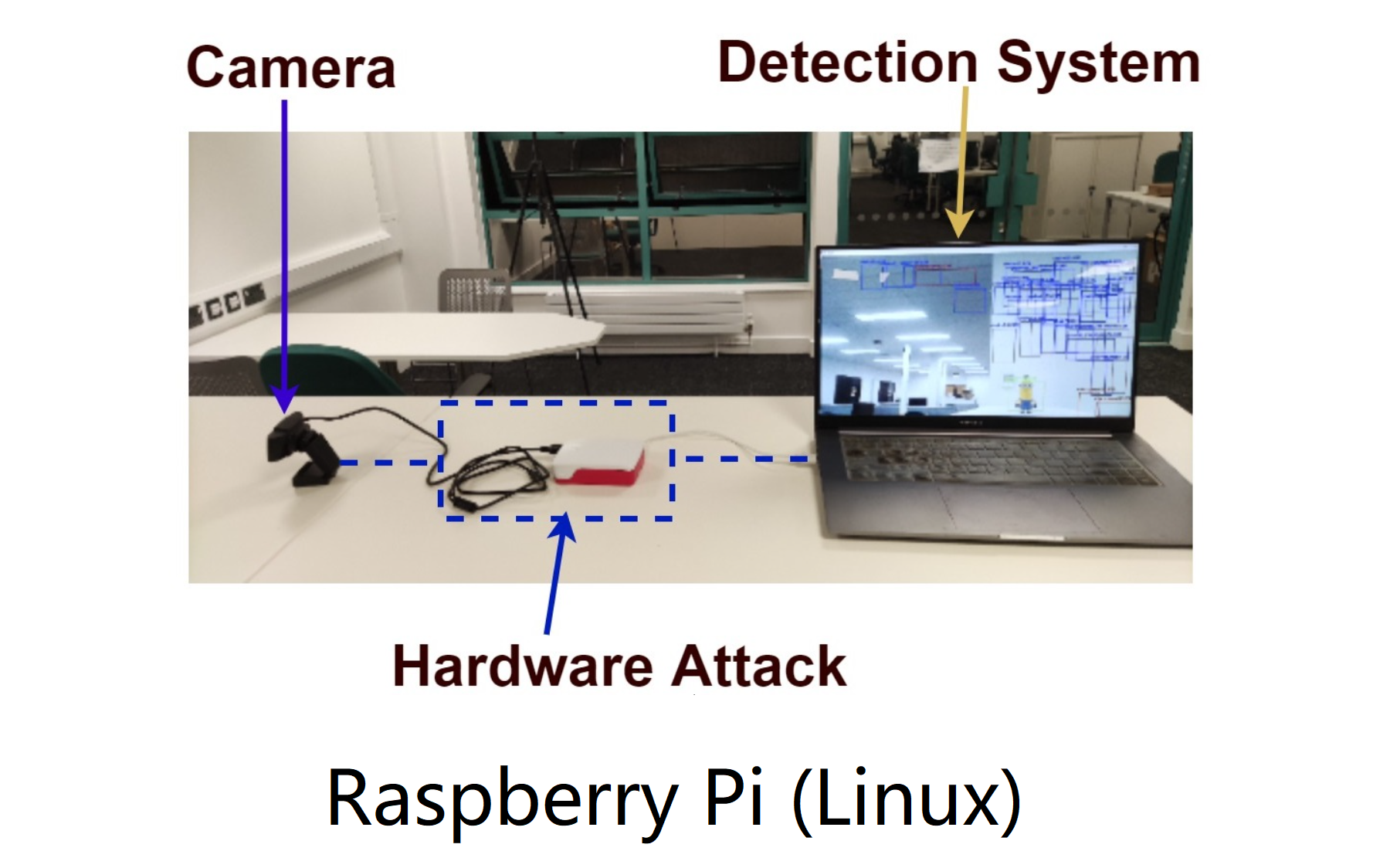
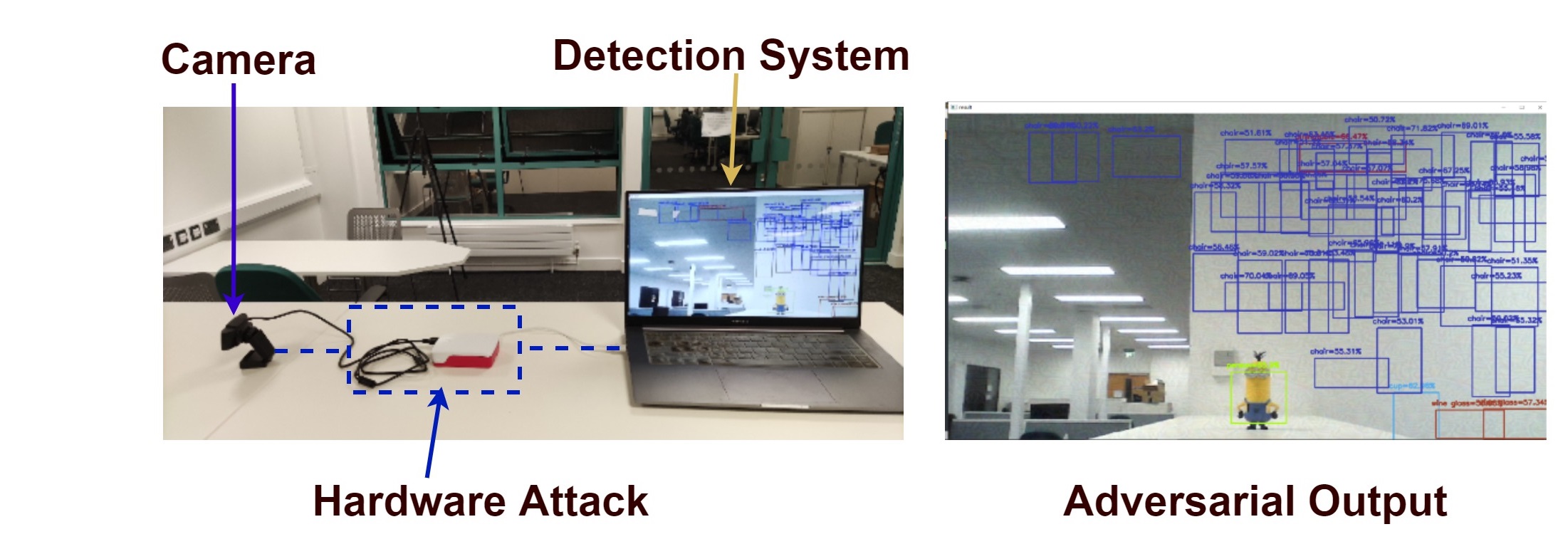
Man-in-the-Middle Attack
A hardware attack against Object Detection.
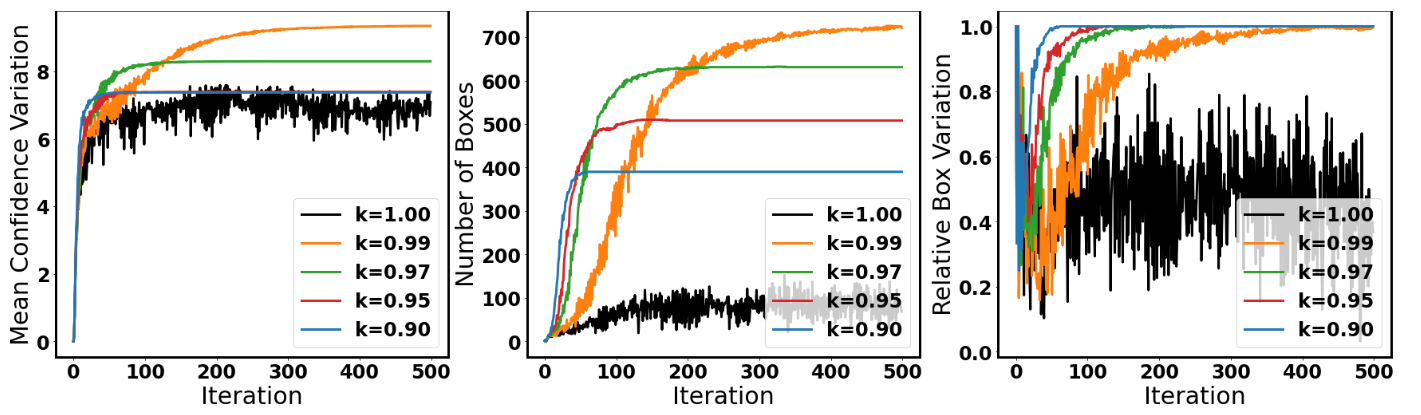
Step 1: Generating the perturbation
Prior Research
Our Method
No learning rate decay
With learning rate decay
Our method generates more bounding boxes, and have less variation.
Step 2: Applying the perturbation
From Linux to RT-Thread Smart
From Monolithic to Microkernel RTOS
From RT-Smart to RT-Thread
From High-End Devices to Middle-End Devices.
Adversarial Classification
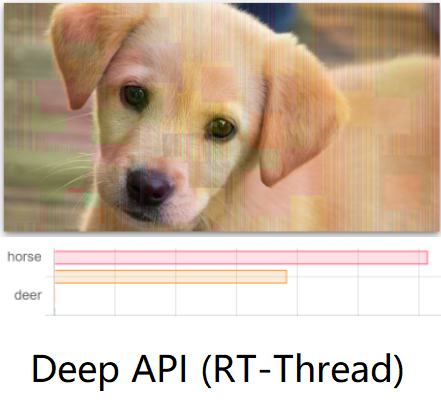
Attacking Image Classification Cloud Services.
Demo: DeepAPI via RT-Thread
Access Image Classification Cloud Service on MCU.
Deep Learning Models are vulnerable to Adversarial Attacks.
High-End: Linux
High-End: RT-Smart
Middle-End: RT-Thread
IoT Devices consist of High-End, Middle-End, and Low-End Devices.
Thanks
RT-Thread Community
https://iot.wuhanstudio.uk
Research Website

 Autonomous Driving: The IoT in Automotive
Autonomous Driving: The IoT in Automotive